Hack The Box Write-Up SalineBreeze-1
About SalineBreeze-1
In this post, I’m writing a write-up for the Sherlock challenge SalineBreeze-1 from Hack The Box. Engage in thrilling investigative challenges that test your defensive security skills. With Sherlocks you will be asked to dive into the aftermath of a targeted cyber attack and unravel the dynamics behind them, based on the knowledge provided.
Sherlock Info
| Sherlock : | SalineBreeze-1 |
| Difficulty: | Very Easy |
| Release Date: | 21 Aug 2025 |
| Creator: | VivisGhost |
Your manager has just informed you that, due to recent budget cuts, you’ll need to take on additional responsibilities in threat analysis. As a junior threat intelligence analyst at a cybersecurity firm, you’re now tasked with investigating a cyber espionage campaign linked to a group known as Salt Typhoon. Apparently, defending against sophisticated Nation-State cyber threats is now a “do more with less” kind of game. Your Task: Conduct comprehensive research on Salt Typhoon, focusing on their tactics, techniques, and procedures. Utilize the MITRE ATT&CK framework to map out their activities and provide actionable insights. Your findings could play a pivotal role in fortifying our defenses against this adversary. Dive deep into the data and show that even with a shoestring budget, you can outsmart the cyber baddies.
Resources
There are no resources provided with this challenge.
Investigation
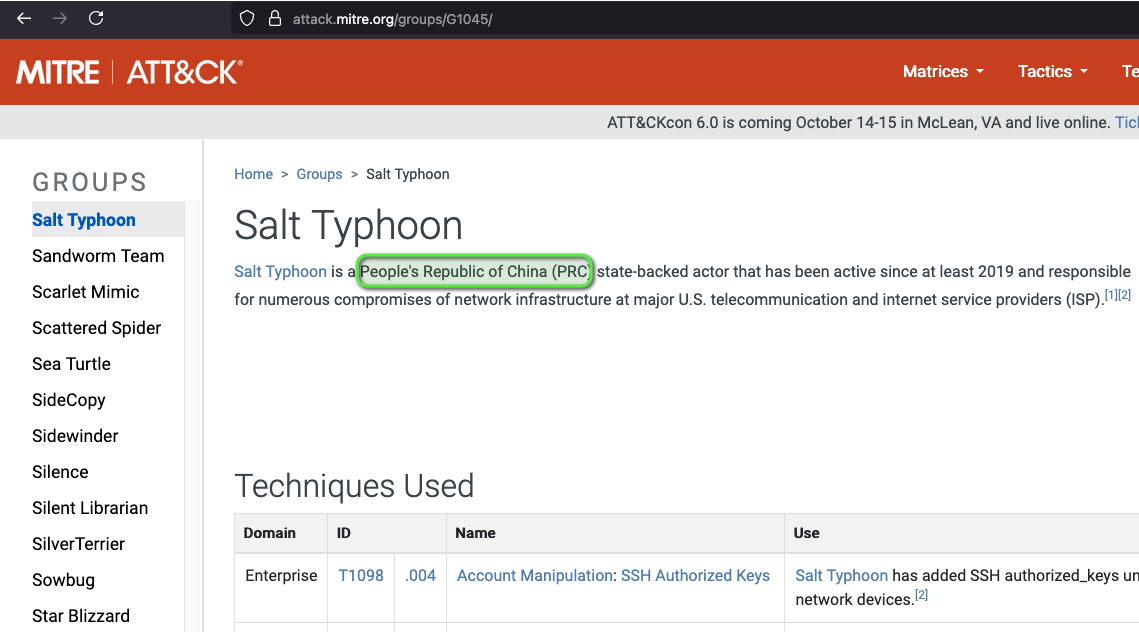
- Starting with the MITRE ATT&CK page, which country is thought be behind Salt Typhoon?
Start with the Google search mitre attack Salt Typhoon and landed on the following page https://attack.mitre.org/groups/G1045/, and on this website we can see that this malware campaign is from a state-backed actof from China.
- According to that page, Salt Typhoon has been active since at least when? (Year)
From the same page, also visible in the screenshot above, that
-
What kind of infrastructure does Salt Typhoon target?
-
Salt Typhoon has been associated with multiple custom built malware, what is the name of the malware associated with the ID S1206?
-
What operating system does this malware target?
-
What programming language is the malware written in?
-
On which vendor’s devices does the malware act as a network sniffer?
-
The malware can perform ‘Indicator Removal’ by erasing logs. What is the MITRE ATT&CK ID for this?
-
On December 20th, 2024, Picus Security released a blog on Salt Typhoon detailing some of the CVEs associated with the threat actor. What was the CVE for the vulnerability related to the Sophos Firewall?
-
The blog demonstrates how the group modifies the registry to obtain persistence with a backdoor known as Crowdoor. Which registry key do they target?
-
What is the MITRE ATT&CK ID of the previous technique?
-
On November 25th, 2024, TrendMicro published a blog post detailing the threat actor. What name does this blog primarily use to refer to the group?
-
The blog post identifies additional malware attributed to the threat actor. Which malware do they describe as a ‘multi-modular backdoor…using a custom protocol protected by Transport Layer Security’
-
Most of the domains the malware communicates with have a .com top-level domain. One uses a .dev TLD. What is the full domain name for the .dev TLD?
-
What is the filename for the first GET request to the C&C server used by the malware?
-
On September 30th, 2021, a blog post was released on Securelist by Kaspersky. What was the threat actor’s name at that time?
-
What is the name of the malware that this article focuses on?
-
What type of malware is the above malware?
-
The first stage consists of a malicious PowerShell dropper. What type of encryption is used to obfuscate the code?
-
The malware uses Input/Output Control codes to perform various tasks related to hiding malicious artifacts. What is the IOCTL code used by the malware to hide its service from the list within the services.exe process address space?
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy researching :-)